By Steven Viney.
The dark net has continued to make headlines over the last decade as a mysterious part of the internet where criminals lurk and engage in illegal activities, all from the privacy of home computers.
Stories of the infamous Silk Road drug market, where users can order illicit drugs online, may come to mind. Or perhaps you have heard about the anonymous digital currency, Bitcoin.
But for all that is written about the dark net, most people would be hard-pressed to explain it.
Here is a simple, user-friendly explainer of what it is, how it is used, and the questions it raises as we drift deeper into the digital age.
What is the dark net?
The dark net generally means using the internet in a manner that is difficult for authorities or non-state actors to monitor. This is usually achieved through encryption or by layering networks.
What is encryption?
-
Digital encryption is used to enhance the security of a message or file
-
It does this by scrambling a code according to a unique key, making it unreadable without it
-
Two users carrying the same key can then transfer coded messages
-
PGP websites and online software allow users to create a key and code messages
-
It is estimated it would take billions of years and thousands of computers to break well-encrypted data
-
Applications such as Tor, Chrome, Firefox, and iMessage on iPhones all have encryption built-in
It might sound complicated, but for the majority of dark net users this is done simply with software that is downloaded for free and opened, just like ordinary, everyday software.
For example, most internet users would not know how to manually “mine” server databases in order to index websites based on keywords. But everyone knows how to use Google, and dark net applications aim to be just as user friendly.
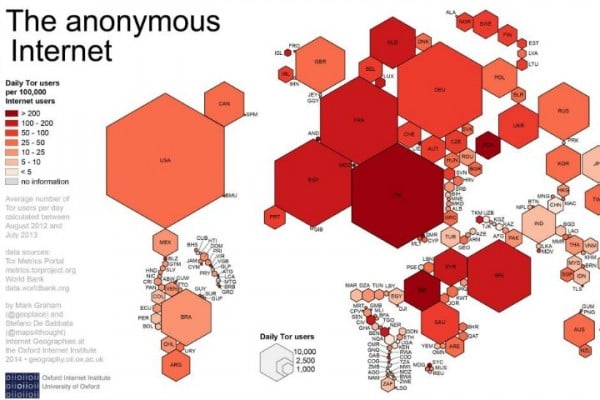
For website browsing, users can simply download a browser called Tor, for free, through which they can anonymously access a variety of websites not normally available on commercial browsers.